Remote Desktop Services ed eventi di Errore TermDD 56 e 50
Andando a controllare l’Event Viewer di un server RDS Windows Server 2008 R2 può succedere di riscontrare gli eventi di errore TermDD con ID 56 o 50 nel registro di sistema.
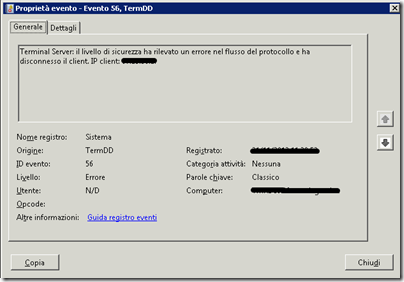
Errore TermDD 56
Questo errore è descritto nel seguente post The Curious Case of Event ID: 56 with Source TermDD del blog dell’EPS Windows Server Performance Team.
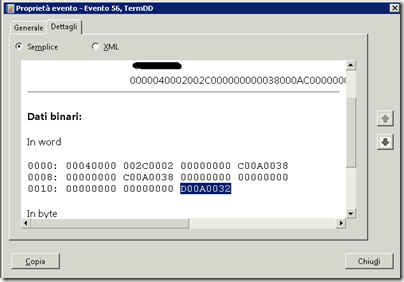
Come spiegato nel post per analizzare le cause le problema bisogna analizzare l’ultima DWORD dei dati binari visualizzati in word.
Nell’esempio riportato in figura l’ultima DWORD è D00A0032 per ottenere il codice d’errore occorre sostituire la D iniziale con la C in quanto la D viene ottenuta come risultato della conversione di un codice NTSTATUS in HRESULT.
Quindi nell’esempio riportato in figura il codice d’errore sarà C00A0032 che potremo analizzare mediante il tool Microsoft Exchange Server Error Code Look-up.
Di seguito alcuni risultati della ricerca su vari codici d’errore:
C00A0032 – STATUS_RDP_PROTOCOL_ERROR – The RDP protocol component %2 detected an error in the protocol stream and has disconnected the client.
C00000B5 – STATUS_IO_TIMEOUT – The connection has timed out.
C000006F – STATUS_INVALID_LOGON_HOURS – The user account has time restrictions and may not be logged onto at this time.
80090330 – SEC_E_DECRYPT_FAILURE – The data on the wire got corrupted.
Per maggiori dettagli si veda il post che ho citato precedentemente The Curious Case of Event ID: 56 with Source TermDD.
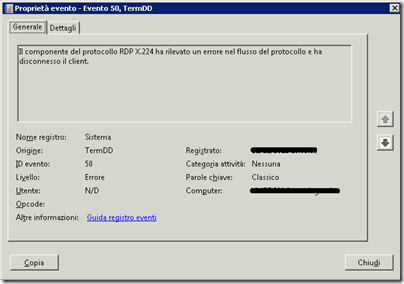
Errore TermDD 50
Questo errore viene analizzato nel post How to troubleshoot “The Terminal Server security layer detected an error in the protocol stream and has disconnected the client. Client IP:” and “The RDP protocol component X.224 detected an error in the protocol stream and has disconnected the client”err.
La causa può essere dovuta all’incompatibilità con le funzionalità di TCP Chimney Offload, Receive Side Scaling (RSS) e Network Direct Memory Access (NetDMA) e nel post viene indicato appunto la procedura per disabilitare il TCP Chimney Offload sia a livello di sistema operativo che di scheda di rete e per disabilitare RSS e NetDMA a livello di sistema operativo.
“1) Configure TCP Chimney Offload in the operating system
To disable TCP Chimney Offload, follow these steps:
a. Use administrative credentials to open a command prompt.
b. At the command prompt, type the following command, and then press ENTER:
netsh int tcp set global chimney=disabled2) Configure TCP Chimney Offload on the network adapter
To determine the current status of TCP Chimney Offload, follow these steps:
a. Use administrative credentials to open a command prompt.
b. At the command prompt, type the following command, and then press ENTER:
netsh int tcp show globalTo determine the current status of TCP Chimney Offload, follow these steps:
a. Use administrative credentials to open a command prompt.
b. At the command prompt, type the following command, and then press ENTER:
netsh int tcp show global3) Disable RSS in Windows Server 2008 R2
To disable RSS, follow these steps:
1. Use administrative credentials to open a command prompt.
2. At the command prompt, type the following command, and then press ENTER:
netsh int tcp set global rss=disabledTo determine the current status of RSS, follow these steps:
a. Use administrative credentials to open a command prompt.
b. At the command prompt, type the following command, and then press ENTER:
netsh int tcp show global4) Disable NetDMA in Windows Server 2008 R2
To disable NetDMA, follow these steps:
1. Click Start, click Run, type regedit, and then click OK.
2. Locate the following registry subkey, and then click it:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
3. Double-click the EnableTCPA registry entry.
Note If this registry entry does not exist, right-click Parameters, point to New, click DWORD Value, type EnableTCPA, and then press ENTER.
4. To enable NetDMA, type 1 in the Value data box, and then click OK.
5. To disable NetDMA, type 0 in the Value data box, and then click OK.
6. If the EnableTCPA registry entry does not exist, enable the NetDMA functionality.”
A riguardo si vedano anche il seguente post The effect of TCP Chimney offload on viewing network traffic e la seguente discussione Remote Desktop client connection to Windows Server 2008 R2 disconnects at random intervals in cui l’utente che lamentava il problema delle disconnessioni asserisce di aver risolto con le seguenti configurazioni:
“A. Open DOS Console and execute the following commands:
– “Netsh int tcp set global chimney=Disabled”.
– “Netsh int tcp set global rss=Disabled”.B. Run Regedit.exe and make the following changes:
Navigate to “HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server”.
– Set “fDenyTSConnections” = 0.C. Open Network Connections Manager (ncpa.cpl), right click each active “Local Area Connection”,
select “Properties”,click “Configure” button, then make the following changes:On the “Advanced” tab disable all “Offload” properites. Below are a couple
of examples.Example #1 (Dell PowerEdge R410):
– Set “Large Send Offload Version 1 (IPv4)” = Disabled.
– Set “Large Send Offload Version 2 (IPv6)” = Disabled.
– Set “TCP/UDP Checksum Offload (IPv4)” = Disabled {original value = Rx & Tx Enabled}.
– Set “TCP/UDP Checksum Offload (IPv6)” = Disabled {original value = Rx & Tx Enabled}.Example #2 (Dell PowerEdge 2950):
– Set “IPv4 Checksum Offload” = None {original value = Tx/Rx Enabled}.
– Set “IPv4 Large Send Offload” = Disable.
– Set “TCP Connection Offload (IPv4)” = Disable.D. Recommend that you reboot the server.”