Raccomandazioni per la lunghezza della chiave dei certificati digitali e del periodo di validità
Quando si creano dei certificatio digitali occorre prestare attenzione alla lunghezza della chiave in relazione al periodo di validità dello stesso.
Ovviamente aumentare la lunghezza della chiave oltre a diminuire il rischio di compromissione del certificato aumenta l’utilizzo della CPU durante gli handshake SSL e la durata dello stesso, questo significa che una chiave più lunga può impattare sulle performace, a riguardo si veda ad esempio il post So you’re making an RSA key for an HTTPS certificate. What key size do you use?.
Se però si decide di utilizzare chiavi di lunghezza minore occorre scegliere una durata del certificato idonea come descritto nel post Recommendations for PKI Key Lengths and Validity Periods with Configuration Manager che nel 2009 riportava le seguenti informazioni basate su una ricerca condotta dall’RSA:
– Key length of 1024: Validity period = not greater than 6-12 months
– Key length of 2048: Validity period = not greater than 2 years
– Key length of 4096: Validity period = not greater than 16 years
E’ possibiole reperire ulteriori informazioni in merito nella sezione Key Management del NIST (National Institute of Standards and Technology) dove nel documento Special Publication (SP) 800-57, Part 1 Rev. 4, Recommendation for Key Management, Part 1: General del Gennaio 2016 è possibile reperire le seguenti indicazioni:
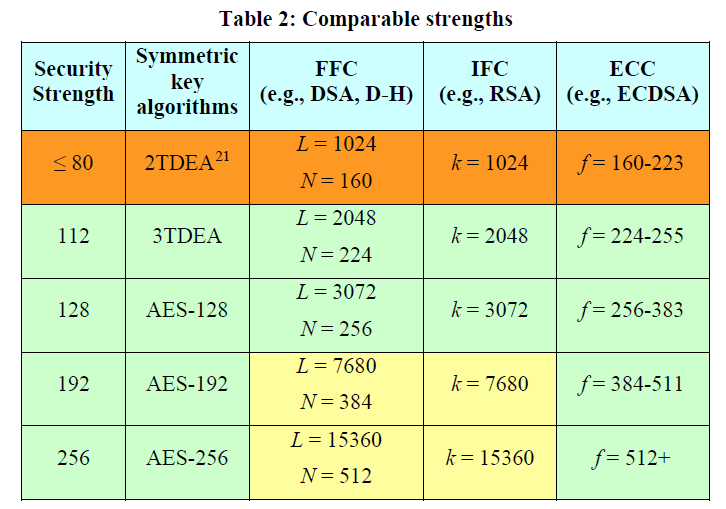
Note that the 192-bit and 256-bit key strengths identified for the FFC and IFC algorithms (shaded in yellow) are not currently included in the NIST standards for interoperability and efficiency reasons.
Also, note that algorithm/key-size combinations that have been estimated at a maximum security strength of less than 112 bits (shaded in orange above) are no longer approved for applying cryptographic protection on Federal government information (e.g., encrypting data or generating a digital signature). However, some flexibility is allowed for processing already-protected information at those security strengths (e.g., decrypting encrypted data or verifying digital signatures) if the receiving entity accepts the risks associated with doing so.
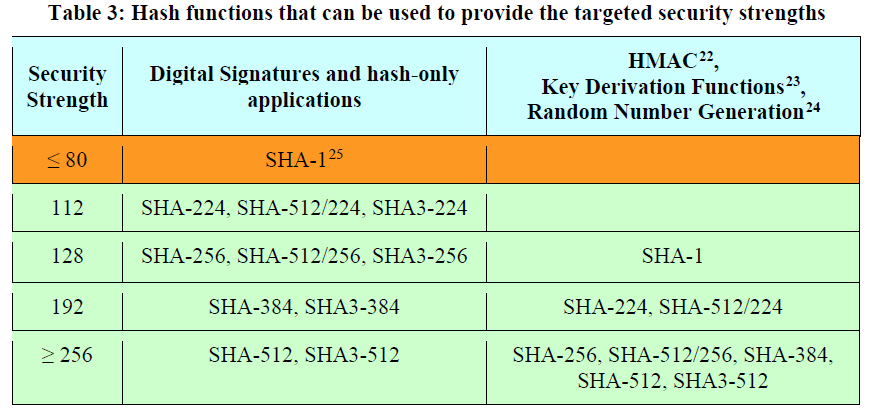
Note that hash functions and applications providing less than 112 bits of security strength (shaded in orange) are no longer approved for applying cryptographic protection on Federal government information (e.g., generating a digital signature). However, some flexibility is allowed for processing already-protected information at those security strengths (e.g., verifying digital signatures), if the receiving entity accepts the risks associated with doing so.
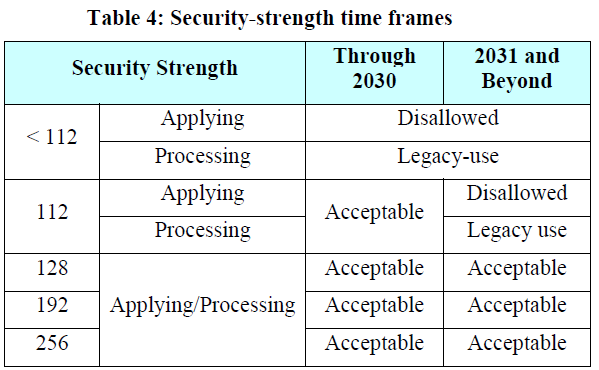
Column 1 is divided into two sub-columns. The first sub-column indicates the security strength to be provided; the second sub-column indicates whether cryptographic protection is being applied to data (e.g., encrypted), or whether cryptographically protected data is being processed (e.g., decrypted).
Columns 2 and 3 indicate the time frames during which the security strength is either acceptable, OK for legacy use or disallowed26.
- “Acceptable” indicates that the algorithm or key length is not known to be insecure.
- “Legacy-use” means that an algorithm or key length may be used because of its use in legacy applications (i.e., the algorithm or key length can be used to process cryptographically protected data).
- “Disallowed” means that an algorithm or key length shall not be used for applying cryptographic protection.
If the security life of information extends beyond one time period specified in the table into the next time period (the later time period), the algorithms and key sizes specified for the later time period shall be used for applying cryptographic protection (e.g., encryption). The following examples are provided to clarify the use of the table:
Da cui si può trarre le seguente conclusione: per un certificato con lunghezza della chiave di 2048 e algoritmo di hash SHA-224 il periodo di validità non deve superare il 2030.
